How To Set Up an SSH Key For Secure Connections
The Secure Shell Protocol (SSH) is perhaps the most well-known means of establishing a secure connection between a client computer (your laptop, phone or desktop) and a remote server in an office, data center or on your home network. You will probably use SSH if you want to access the command line of your web hosting service or a headless Raspberry Pi. SSH is available in some form for almost every operating system and is often built into the operating system.
Most servers give you the choice to connect to SSH using a password or using SSH keys, which are more secure. The SSH key method uses cryptographically generated public and private keys to establish an encrypted connection between devices.
Our public key is stored on the remote computer and a private key is stored on our computer. The two SSH keys are required to establish a secure connection. Keys can also be used with passphrases to add another layer of security, but they can also be used without, for example in automated processes.
This guide will show you how to create SSH keys using PuTTY, the most popular SSH client, and in Windows Command Prompt / Linux Terminal.
Preparing the remote server for SSH keys
Our remote computer may be located in a data center operated by a web hosting service, at our office, or at home. Typically, Linux servers like VPS and cloud hosting run SSH by default, using passwords for secure logins. If not, you will need to enable SSH from the Control Panel for your VPS/Cloud service. If you are using a home server, it may not be installed. If so, follow these steps before proceeding.
1. Open a terminal and check if the computer has an SSH service running. If the SSH service is running, it returns Active: active (running).
sudo service ssh status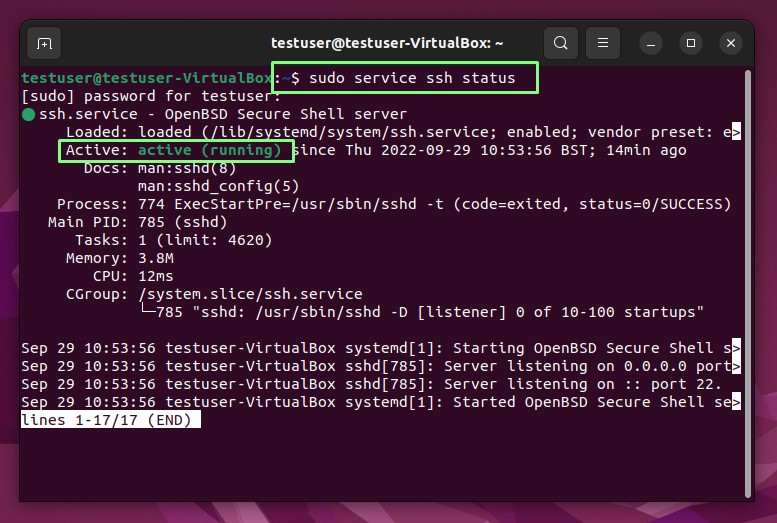
2. On the physical server, open a terminal and install OpenSSH Server. You must be in front of the machine to issue these commands.
sudo apt update
sudo apt install openssh-server3. Start the SSH service.
sudo service ssh start4. Create a hidden directory called .ssh in your home directory.
mkdir .ssh5. Close the connection by pressing CTRL+D or by typing exit and pressing Enter.
Using PuTTY to connect to a remote server using SSH keys
PuTTY is an application for creating and managing SSH and serial connections to devices. PuTTY comes with its own key generator application and in this part of the guide we will create a public key for our remote server and a private key on our trusted device.
1. Download and install PuTTY. While Windows has its own command prompt that can be used with SSH, PuTTY is by far the most accessible means of opening an SSH connection.
2. Search for puttygen and open the application.
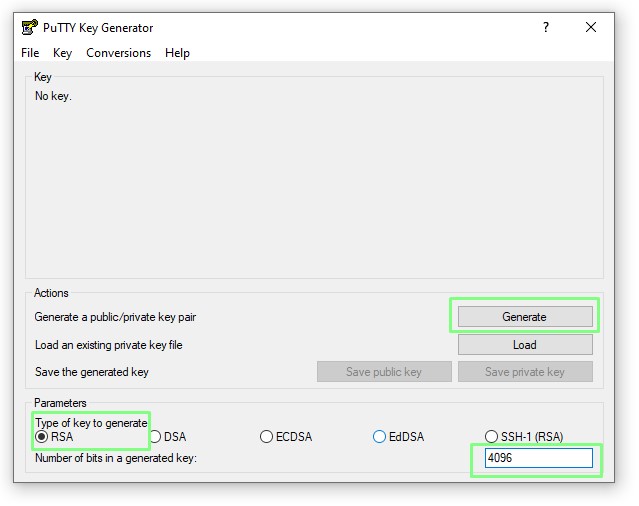
3. Click RSA and set the bits to 4096. Click Generate to create a key.
4. Hover the mouse over the blank area of the dialog box to generate a random seed for the key.
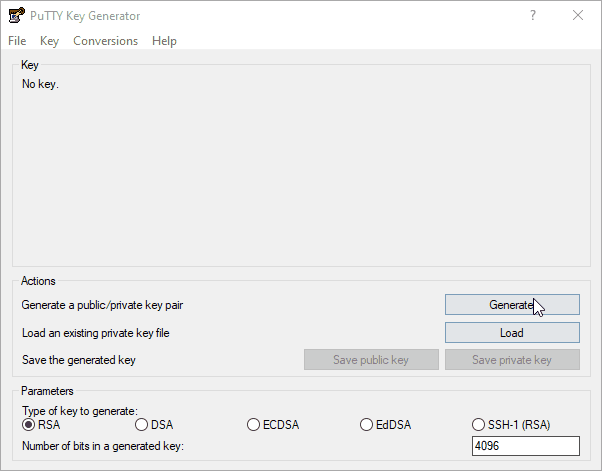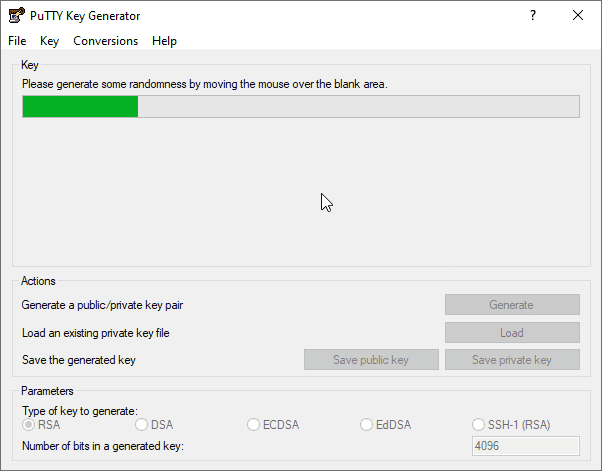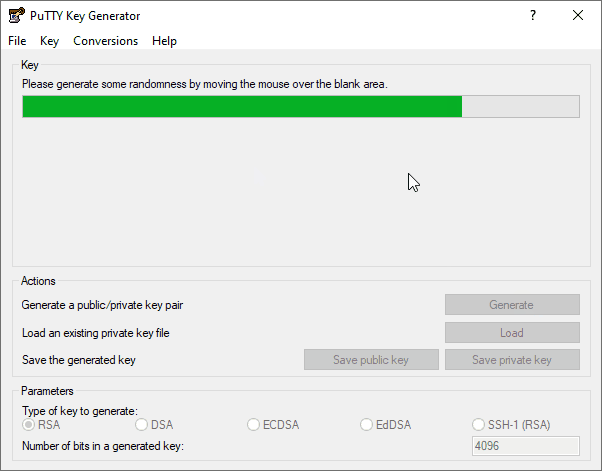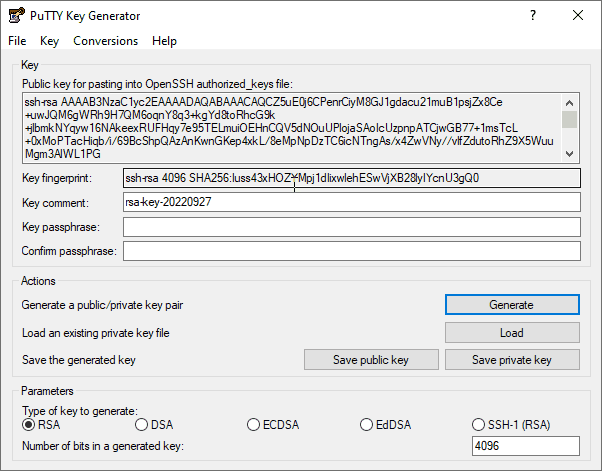
5. Create a passphrase for the key. This is recommended for SSH keys used in interactive sessions.
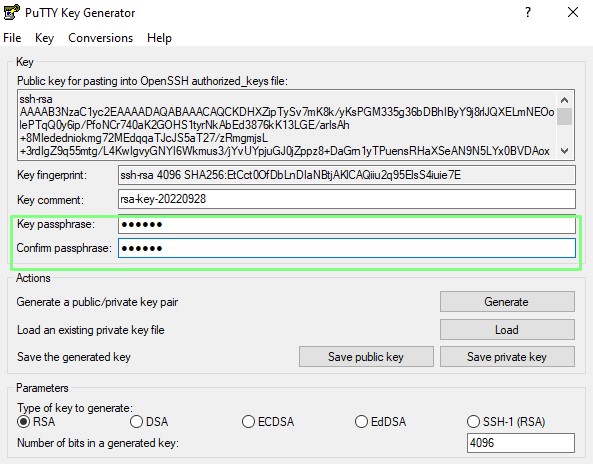
6. Save the public key as id_rsa_putty.pub in a folder called .ssh.
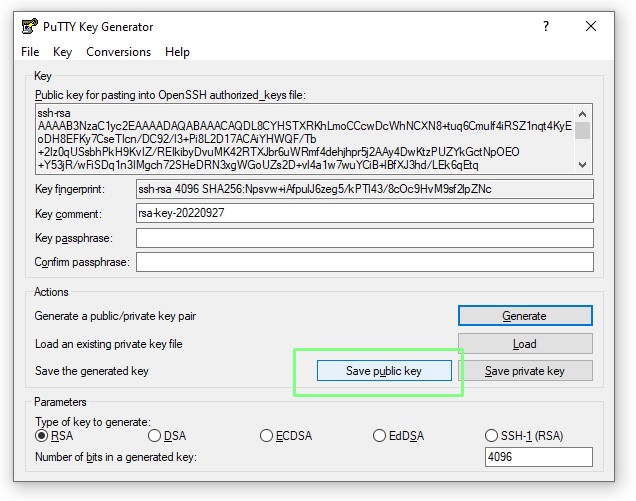
7. Save the private key as id_rsa_putty.ppk. The ppk file is Putty’s own private key format.
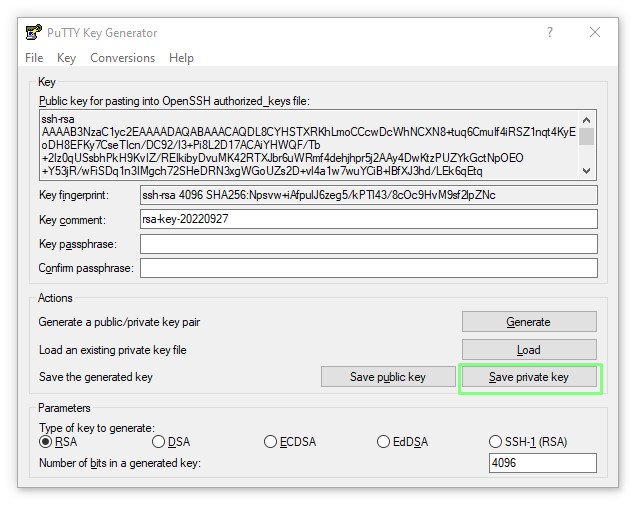
8. Highlight the public key and copy the text.
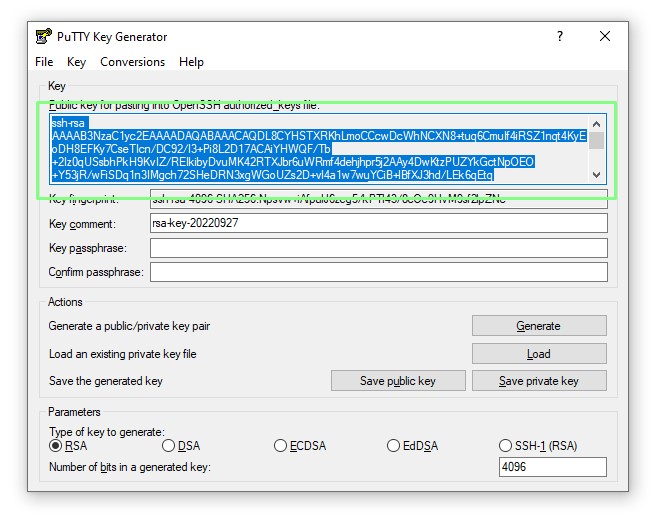
Copying the public key to the remote server
1. Start PuTTY.
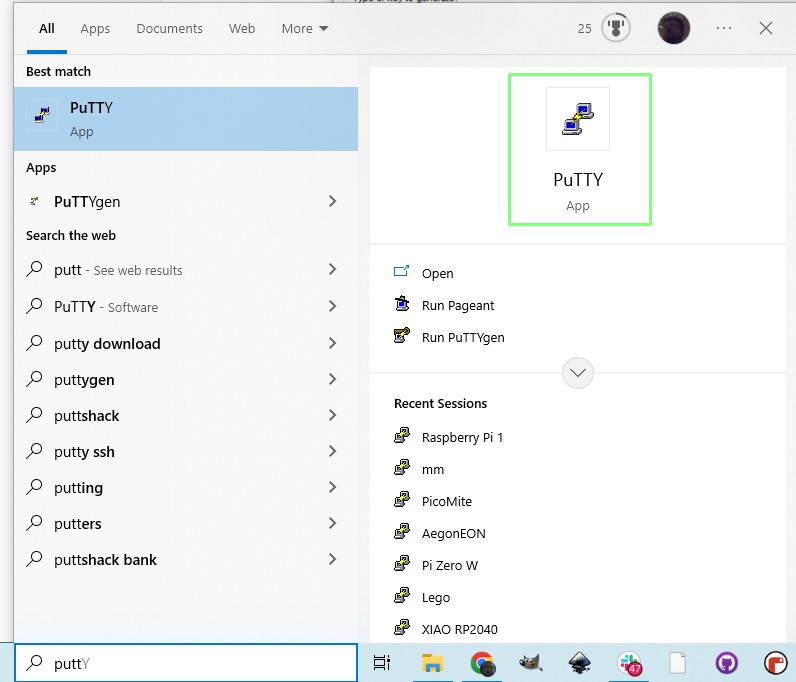
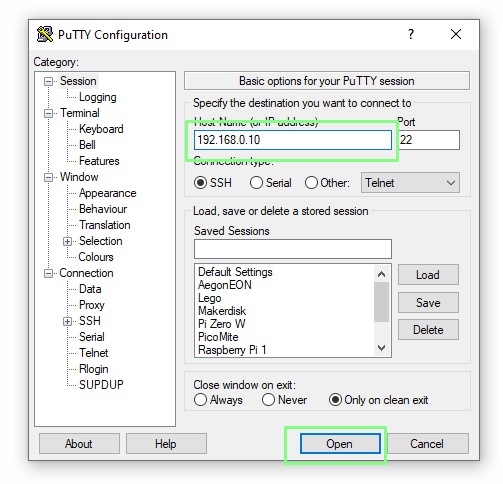
2. Enter the IP address or hostname for your remote server and click Open.
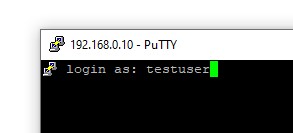
3. If prompted, enter your username and password for the remote server. Note that the password is not displayed. This is a security feature to prevent “shoulder surfing”.
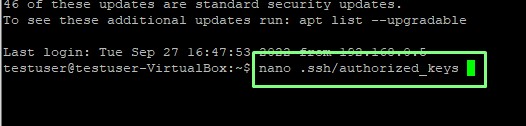
4. Using the nano text editor, create a new file named “authorized_keys” in the “.ssh” directory.
5. Right click and paste the public key (created in PuTTYGen) into the empty file. Save on computer by pressing CTRL+X, then Y and Enter.
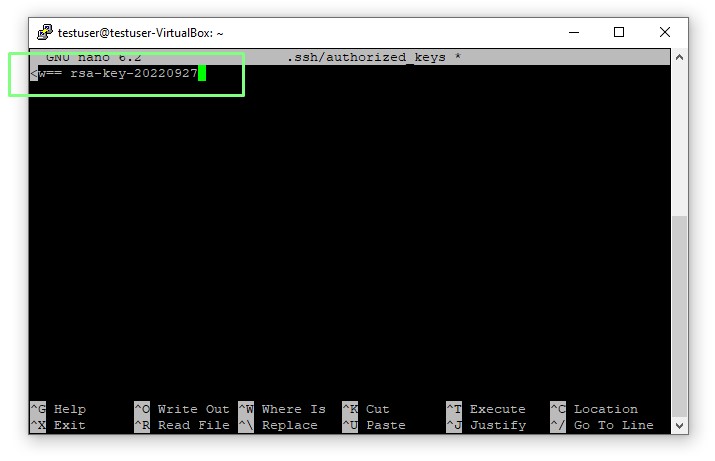
6. Log out of the SSH session by pressing CTRL + D.
7. Reopen PuTTY and Go to SSH >> Auth.
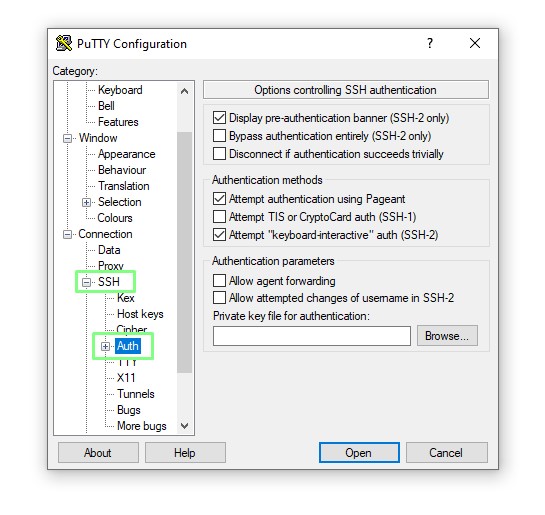
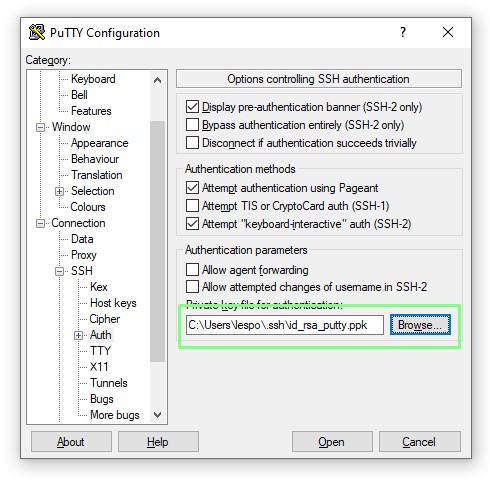
8. Select the Putty Private Key (ppk). that we just created.
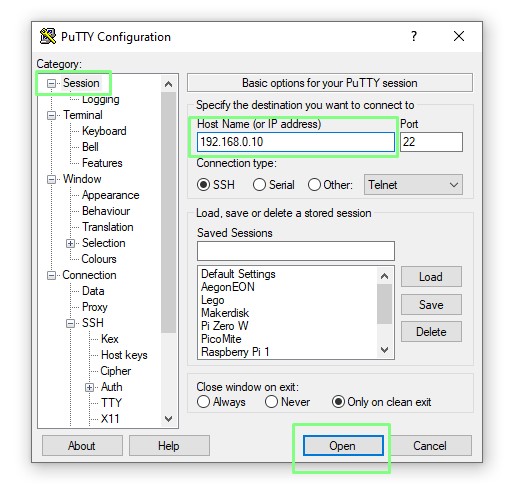
9. Scroll back to Session and enter the hostname/IP address for your server and click Open to start a connection.
10. Enter your username and then the passphrase for your key. Press Enter to log in.
You are now in control of the remote server using a Linux terminal working on the Linux file system. To close a connection, use CTRL + D or click the X to close the window.
How to create an SSH key pair from command prompt/terminal
Creating an SSH key pair from the command prompt/Linux terminal can be done with just one command and a few questions to answer. We set up the public and private keys on our client machine and copy the public key to the remote server. These steps apply to the Windows command prompt and the Linux terminal.
1. Open a command prompt by pressing the Windows key and searching for CMD. Press Enter to run.
2. Use the ssh-keygen command to create an SSH key with the key type RSA with 4096 bits.
ssh-keygen -t rsa -b 4096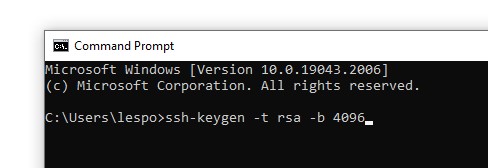
3. When prompted to name your key, press Enter. This will save the private and public keys in the .ssh directory for your named account. For example, our keys were stored in C:\Users\lespo\.ssh. Linux users store the keys in .ssh in their home directory \home\user\.ssh
4. When prompted, For an extra layer of security, give your key a passphrase. A passphrase is an extra security step for SSH keys used by real users (interactively). A passphrase is not required when the SSH connection is used in an automated script.
5. Browse to the directory where you saved your SSH keys. Here we assume you are in your named account. For example, C:\Users\lespo is ours. On Linux it would be /home/les/.ssh
cd .ssh6. List the files in the directory. There should be id_rsa and id_rsa.pub.
Windows Command
dir
Linux Command
ls
Copying the public key to the remote server
The public key is stored on our remote server and interacts with the private key on our trusted computer to create a secure connection. In order to get the public key on our server, we need to securely copy (scp) the file over there.
1. From a command prompt, use the scp command to safely copy the id_rsa.pub file to your home directory on the remote server. You need to know the IP address or hostname of the remote computer. In our example, we copied the file to [email protected]:/home/testuser/.
scp id_rsa.pub user@hostname:/home/username2. SSH into the remote computer.
ssh user@hostname3. Make sure the id_rsa.pub file exists in your home directory.
ls *.pub4. Copy the contents of the file to a new file in the .ssh directory. With the cat command we send the contents to the file,authorized_keys with a pipe appending the data to the file (>>).
cat id_rsa.pub >> .ssh/authorized_keys5. Close the SSH connection by pressing CTRL + D or typing exit.
6. Reconnect to the remote computer via SSH. If you’ve created a passphrase for your SSH key, you’ll be prompted to do so.
Using SSH keys on another computer
Reusing your private SSH key is possible, but not the best security practice. Losing a laptop with the key means you will need to regenerate your keys. Best practice would be to generate a new key pair for each device trying to connect. Appending the public key to the authrozied_keys file on the server. However, it is relatively easy to reuse a private key on multiple devices.
Reusing a PuTTY private key
PuTTY stores the private key as a PPK key and this file is all we need for a machine to connect to a remote server with our public key.
1. Go to your .ssh folder and copy the PPK file to a USB stick. Keep this USB stick safe as anyone can use it to gain access to your server.
2. Insert the USB stick into another computer.
3. Create a .ssh folder in your home directory. For Windows this would be C:\Users\username\.ssh and Linux /home/user/.ssh.
4. Copy the PPK file to the .ssh directory.
5. Follow from step 7 of copying the public key to the remote server to login.
Reusing a command prompt/terminal private key
1. Go to your .ssh folder and copy the private key file to a USB stick. Keep this USB stick safe as anyone can use it to gain access to your server.
2. Insert the USB stick into another computer.
3. Create a .ssh folder in your home directory. For Windows this would be C:\Users\username\.ssh and Linux /home/user/.ssh.
4. Copy the private key file to the .ssh directory.
5. Start an SSH session with the remote computer. If you’ve created a passphrase for your SSH key, you’ll be prompted to do so.
ssh user@hostname