How to configure and customize Kali Linux
Penetration testing helps determine if there are vulnerabilities and vulnerabilities in corporate systems. A number of pentesting tools are available, including the Kali Linux distribution, which provides everything an ethical hacker needs to effectively test an organization’s systems.
in the Mastery of Kali Linux for advanced penetration testing, author and security practitioner Vijay Kumar Velu, provides detailed instructions on testing a network running Kali Linux. Readers will learn how to choose the best tools from the distribution to compromise security while remaining undetected by services or users.
For those starting out with Kali Linux, follow the excerpt from Chapter 1 of Mastering Kali Linux to learn how to organize and customize Kali Linux for the first time. Download a PDF of Chapter 1 here.
Watch a Q&A where Velu explains how pentesters of all skill levels can use his book, why it’s worth using Kali Linux for offensive security, and more.
Organize Kali Linux
Installation is just the beginning; Organizing Kali Linux is a very important next step. In this section we will examine the different ways in which our Kali Linux can be organized through customization.
Configuring and customizing Kali Linux
Kali is a framework used to perform penetration testing. However, the tester should never feel locked into the default installed tools or the look and feel of the Kali desktop. By customizing Kali, a tester can increase the security of collected customer data and make it easier to conduct a penetration test. The general customization options that can be made in Kali include the following:
 learn more about
learn more aboutMaster
Advanced Kali Linux
penetration testing here.
- Kali password reset
- Adding a non-root user
- Configure network services and secure communications
- Adjust network proxy settings
- Access to the secure shell
- Accelerating Kali operations
- Sharing folders with Microsoft Windows
- Create encrypted folders
Now let’s take another look at these options.
Reset default password
If you downloaded the pre-configured VMware or VirtualBox image, the default username and password to access Kali Linux is Kali. It is recommended to change the default password; To do this, run the following command in the Kali Linux terminal:

You will then be prompted to enter a new password and then confirm it.
Configure network services and secure communications
The first step to ensure that we can access the internal network is to ensure that it has a connection to a wired or wireless network to support updates and communication. You may need to get an IP address via Dynamic Host Configuration Protocol (DHCP) by attaching a network configuration file and adding an Ethernet adapter in the form of the following commands from the Kali Linux terminal:

Once the network configuration file is attached, you should be able to use the ifup Script to automatically assign the IP address as shown in Figure 1.28:

Figure 1.28: Successful assignment of an IP address via DHCP using the ifup script
In the case of a static IP, you can append the same network configuration file with the following lines and quickly set up a static IP for your version of Kali Linux:
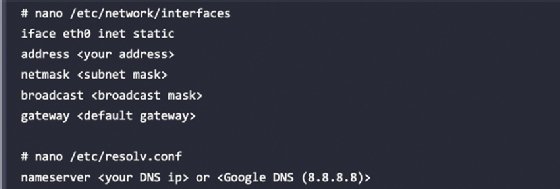
By default, Kali starts with DHCP service enabled. This announces the new IP address to the network, potentially alerting administrators to the tester’s presence. For some test cases this may not be a problem, and it may be beneficial to have certain services start automatically during boot. This can be achieved by entering the following commands:

Kali comes installed with network services that can be started or stopped as needed, including DHCP, HTTP, SSH, TFTP, and the VNC server. These services are typically invoked from the command line; However, some are accessible through the Kali menu.
Adjust network proxy settings
Users who are behind an authenticated or unauthenticated proxy connection must change it bash.bashrc and apt.conf files. Both files are in the /Etc/ Directory. Edit the bash.bashrc File as shown below by using a text editor to add the following lines to the end of the file bash.bashrc File:
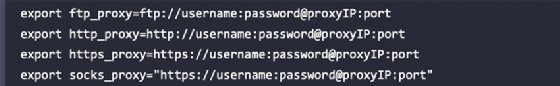
Substitute Proxy IP and Harbor with your proxy IP address or port number and replace the username and password with your username and password for authentication. If no authentication is required, only write the part after the @ Symbol. Save and close the file.
Remote access to the Secure Shell
To minimize detection by a target network during testing, Kali does not enable external listening network services. Some services like SSH are already installed. However, they must be activated before use. Kali comes preconfigured with standard SSH keys. Before starting the SSH service, it’s a good idea to disable the default keys and generate a unique set of keys to use, as the code below shows. Move the default SSH keys to a backup folder, and then generate a new SSH key set with the following command:
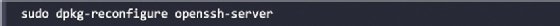
To confirm that the SSH service is running, you can use the command to verify it sudo service ssh status.
Note that the default configuration of SSH has root login disabled. If you need access with the root account, you may need to edit /etc/ssh/sshd_config and adjust Allow root login to Yes indeed, save and then exit. Finally, you should be able to access the SSH service and use Kali Linux from any system on the same network. In this example we use PuTTY, a free and portable SSH client for Windows. Now you should be able to access Kali Linux from another computer, accept the SSH certificate and enter your credentials.
Accelerating Kali operations
Several tools can be used to optimize and speed up Kali operations:
- If you are using a VM, install its software disk pack, either Guest Additions (VirtualBox) or VMware Tools (VMware).
Hint: We need to make sure we’re running apt get update before installation.
- When creating a VM, choose a fixed disk size instead of a dynamically allocated one. Adding files to a hard drive is faster and there is less file fragmentation.
- By default, Kali does not show all applications that are present in the start menu. Any application installed during startup will slow down system data and may affect memory usage and system performance. This can be done by the following commands in the terminal:
- To list all startup services at boot, type sudo systemctl list-unit-files –type=service in the terminal and you can disable the unwanted services by running it sudo systemctl disable –now
- Finally, you can list the enabled services by running sudo systemctl list-unit-files –type=service –state=enabled –all in the end device
- To list all startup services at boot, type sudo systemctl list-unit-files –type=service in the terminal and you can disable the unwanted services by running it sudo systemctl disable –now
Sharing folders with the host operating system
The Kali toolset provides the flexibility to share results with applications residing on different operating systems, most notably Microsoft Windows. The most effective way to share data is to create a folder that can be accessed by both the host OS and the Kali Linux VM guest. When data is placed in a shared folder from the host or VM, it is immediately available through the shared folder to all systems accessing that shared folder. Follow the steps below to create a shared folder:
- Create a folder on the host operating system. In this example it is called kali_share.
- Right-click the folder and select the Split Choose from this menu Split.
- Make sure the file is shared with All and the permission level is set for this share Read Write.
- If you haven’t already done so, install the VMware tools or Virtual Box Guest additions on Kali Linux.
- When the installation is complete, go to the VMware player menu and select Administer and click Virtual machine settings. Look for the menu that activates Shared Folders and select Always activated.
- In the case of Oracle VirtualBox, select the VM and go to settings and select Shared Foldersas shown in Figure 1.29:
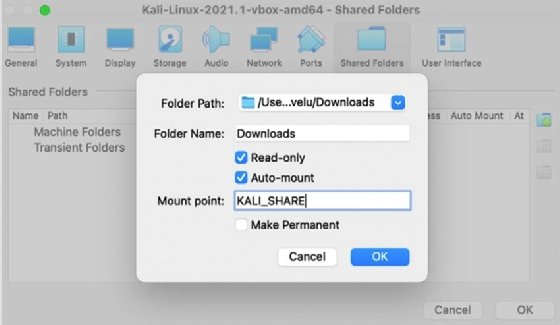
Figure 1.29: Mounting a shared drive from native operating system to guest operating system
Note: Please note that older versions of VMware Player use a different menu.
- Now the folder should be mounted automatically /Media/ folder as shown in Figure 1.30:

Figure 1.30: Successfully mounting the shared drive on the Kali Linux VM
- Anything placed in the folder can be accessed in the folder of the same name on the host operating system and vice versa.
The shared folder containing sensitive data from a penetration test must be encrypted to protect the customer’s network and reduce the tester’s liability if the data is ever lost or stolen.