KamiKakaBot Malware Used in Latest Dark Pink APT Attacks on Southeast Asian Targets
The dark pink Advanced Persistent Threat (APT) Actor has been linked to a new series of attacks targeting government and military facilities in Southeast Asian countries using malware called KamiKakaBot.
Dark Pink, also known as Saaiwc, was first profiled by Group-IB earlier this year and described using custom tools like TelePowerBot and KamiKakaBot to run arbitrary commands and exfiltrate sensitive information.
The threat actor is said to be from the Asia Pacific region and has been active since at least mid-2021, with an increased pace seen in 2022.
“The latest attacks, which took place in February 2023, were almost identical to previous attacks,” Dutch cybersecurity firm EclecticIQ announced in a new report released last week.
“The main difference in the February campaign is that the malware’s obfuscation routine has improved to better evade anti-malware measures.”
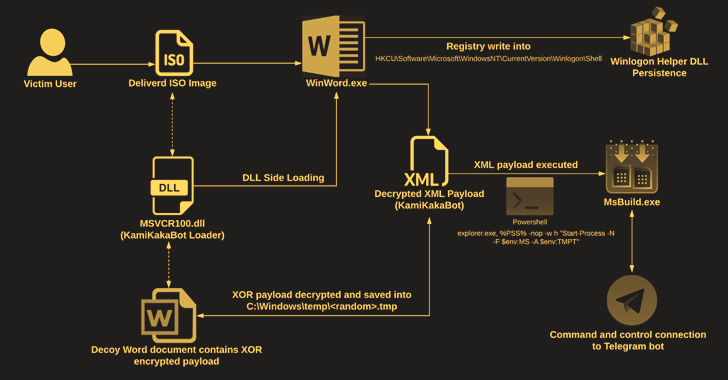
The attacks take the form of socially engineered decoys that include ISO image file attachments in email messages to deliver the malware.
The ISO image contains an executable (Winword.exe), a loader (MSVCR100.dll) and a decoy Microsoft Word document, the latter embedded in the KamiKakaBot payload.
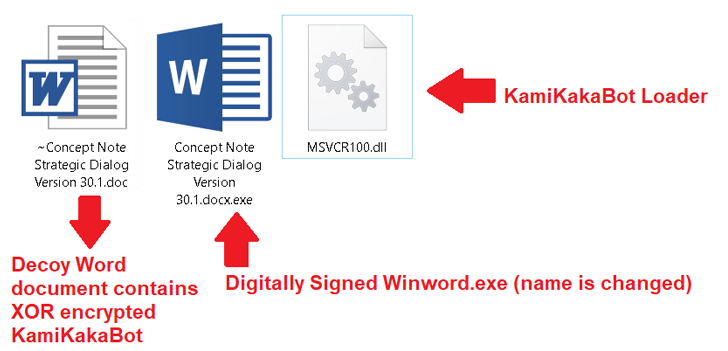
In turn, the loader is designed to load the KamiKakaBot malware using the DLL sideloading method to bypass security measures and load it into the Winword.exe binary’s memory.
KamiKakaBot is primarily designed to steal data stored in web browsers and execute remote code using Command Prompt (cmd.exe), while it also employs evasion techniques to blend into victim’s environment and avoid detection.
Discover the hidden dangers of third-party SaaS apps
Are you aware of the risks associated with third-party app access to your organization’s SaaS apps? Join our webinar to learn about the types of permissions that are granted and how to mitigate risk.
RESERVE YOUR PLACE
Persistence on the compromised host is achieved by abusing the Winlogon helper library to make malicious changes to the Windows registry key. The collected data is then exfiltrated as a ZIP archive to a Telegram bot.
“Using legitimate web services as command-and-control (C2) servers like Telegram remains the top choice for various threat actors ranging from regular cybercriminals to advanced persistent threat actors,” the Amsterdam-based company said.
“The Dark Pink APT group is very likely a cyberespionage-motivated threat actor, specifically exploiting ties between ASEAN and European nations to create phishing lures during the February 2023 campaign.”